A) Log
B) Full Log
C) Detailed Log
D) Extended Log
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this? 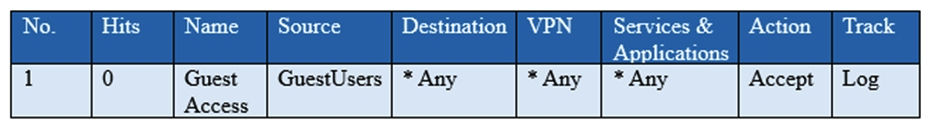
A) Right click Accept in the rule, select "More", and then check "Enable Identity Captive Portal"
B) On the firewall object, Legacy Authentication screen, check "Enable Identity Captive Portal"
C) In the Captive Portal screen of Global Properties, check "Enable Identity Captive Portal"
D) On the Security Management Server object, check the box "Identity Logging"
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have just installed your Gateway and want to analyze the packet size distribution of your traffic with SmartView Monitor.  Unfortunately, you get the message: "There are no machines that contain Firewall Blade and SmartView Monitor" . What should you do to analyze the packet size distribution of your traffic? Give the BEST answer.
Unfortunately, you get the message: "There are no machines that contain Firewall Blade and SmartView Monitor" . What should you do to analyze the packet size distribution of your traffic? Give the BEST answer. 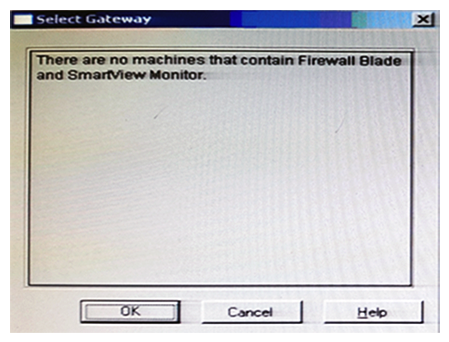
A) Purchase the SmartView Monitor license for your Security Management Server.
B) Enable Monitoring on your Security Management Server.
C) Purchase the SmartView Monitor license for your Security Gateway.
D) Enable Monitoring on your Security Gateway.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blank: RADIUS Accounting gets ______ data from requests generated by the accounting client
A) Destination
B) Identity
C) Payload
D) Location
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT a set of Regulatory Requirements related to Information Security?
A) ISO 37001
B) Sarbanes Oxley (SOX)
C) HIPAA
D) PCI
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In what way are SSL VPN and IPSec VPN different?
A) SSL VPN is using HTTPS in addition to IKE, whereas IPSec VPN is clientless
B) SSL VPN adds an extra VPN header to the packet, IPSec VPN does not
C) IPSec VPN does not support two factor authentication, SSL VPN does support this
D) IPSec VPN uses an additional virtual adapter, SSL VPN uses the client network adapter only
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Using R80 Smart Console, what does a "pencil icon" in a rule mean?
A) I have changed this rule
B) Someone else has changed this rule
C) This rule is managed by check point's SOC
D) This rule can't be changed as it's an implied rule
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What happens if the identity of a user is known?
A) If the user credentials do not match an Access Role, the traffic is automatically dropped.
B) If the user credentials do not match an Access Role, the system displays a sandbox.
C) If the user credentials do not match an Access Role, the gateway moves onto the next rule.
D) If the user credentials do not match an Access Role, the system displays the Captive Portal.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What licensing feature automatically verifies current licenses and activates new licenses added to the License and Contracts repository?
A) Verification tool
B) Verification licensing
C) Automatic licensing
D) Automatic licensing and Verification tool
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
One of major features in R80 SmartConsole is concurrent administration. Which of the following is NOT possible considering that AdminA, AdminB, and AdminC are editing the same Security Policy?
A) A lock icon shows that a rule or an object is locked and will be available.
B) AdminA and AdminB are editing the same rule at the same time.
C) A lock icon next to a rule informs that any Administrator is working on this particular rule.
D) AdminA, AdminB and AdminC are editing three different rules at the same time.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blank: RADIUS protocol uses ______ to communicate with the gateway.
A) UDP
B) TDP
C) CCP
D) HTTP
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Session unique identifiers are passed to the web api using which http header option?
A) X-chkp-sid
B) Accept-Charset
C) Proxy-Authorization
D) Application
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which icon in the WebUI indicates that read/write access is enabled?
A) Pencil
B) Padlock
C) Book
D) Eyeglasses
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT a policy type available for each policy package?
A) Threat Emulation
B) Access Control
C) Desktop Security
D) Threat Prevention
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What does ExternalZone represent in the presented rule? 
A) The Internet.
B) Interfaces that administrator has defined to be part of External Security Zone.
C) External interfaces on all security gateways.
D) External interfaces of specific gateways.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is true about the IPS-Blade?
A) in R80, IPS is managed by the Threat Prevention Policy
B) in R80, in the IPS Layer, the only three possible actions are Basic, Optimized and Strict
C) in R80, IPS Exceptions cannot be attached to "all rules"
D) in R80, the GeoPolicy Exceptions and the Threat Prevention Exceptions are the same
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which option, when applied to a rule, allows traffic to VPN gateways in specific VPN communities?
A) All Connections (Clear or Encrypted)
B) Accept all encrypted traffic
C) Specific VPN Communities
D) All Site-to-Site VPN Communities
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Vanessa is a Firewall administrator. She wants to test a backup of her company's production Firewall cluster Dallas_GW. She has a lab environment that is identical to her production environment. She decided to restore production backup via SmartConsole in lab environment. Which details she need to fill in System Restore window before she can click OK button and test the backup?
A) Server, SCP, Username, Password, Path, Comment, Member
B) Server, TFTP, Username, Password, Path, Comment, All Members
C) Server, Protocol, Username, Password, Path, Comment, All Members
D) Server, Protocol, Username, Password, Path, Comment, Member
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What SmartEvent component creates events?
A) Consolidation Policy
B) Correlation Unit
C) SmartEvent Policy
D) SmartEvent GUI
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server Operating System. He can do this via WebUI or via CLI. Which command should he use in CLI?
A) remove database lock
B) The database feature has one command: lock database override. The database feature has one command: lock database override.
C) override database lock
D) The database feature has two commands: lock database override and unlock database . Both will work. The database feature has two commands: lock database override and unlock database . Both will work.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 61 - 80 of 676
Related Exams